A comprehensive mobile cybersecurity knowledge base to help stakeholders identify, map and mitigate risks
As Mobile Network Operators (MNOs) around the globe introduce and launch 5G systems, while maintaining earlier generation mobile technologies, communications networks will face new security threats and challenges. Understanding, mapping and mitigating these existing and upcoming security threats in an objective, speedy and effective manner has become essential.
To help operators and others in the mobile ecosystem, the GSMA has conducted a comprehensive threat analysis involving industry experts from across the eco-system including MNOs, vendors, service providers, and regulators, as well as collecting input from public sources such as 3GPP, ENISA and NIST, and mapped these threats to appropriate and effective security controls.
The GSMA has collated this analysis into a mobile cybersecurity knowledge base to provide useful guidance on a range of mobile security risks and mitigation measures. The knowledge base aims to make available to GSMA members the combined knowledge of the mobile ecosystem to increase trust in mobile networks and make the interconnected world as secure as possible. Over time, the knowledge base will be enhanced and extended to respond to the evolving cybersecurity threat landscape.
The mobile cybersecurity knowledge base is an industry effort that composes a comprehensive threat landscape designed to help key stakeholders (such as MNOs, equipment vendors, regulators, application developers and service providers) understand the security threats posed by mobile networks in a systematic and objective fashion. It provides essential insights for the stakeholders’ risk management strategy as well as guidance covering best practices and risk mitigation measures.
The knowledge base facilitates and encourages collaboration to protect networks and services against disruption and unauthorised access as well as the prevention and mitigation of risks. The knowledge base will help to enhance mobile security competencies and capabilities and will strengthen the work of carriers, enterprises, oversight agencies and regulators. At an operational level, the knowledge base offers clear instructions for taking step-by-step actions to build security assurance while considering the entire risk spectrum of mobile end-to-end networks.
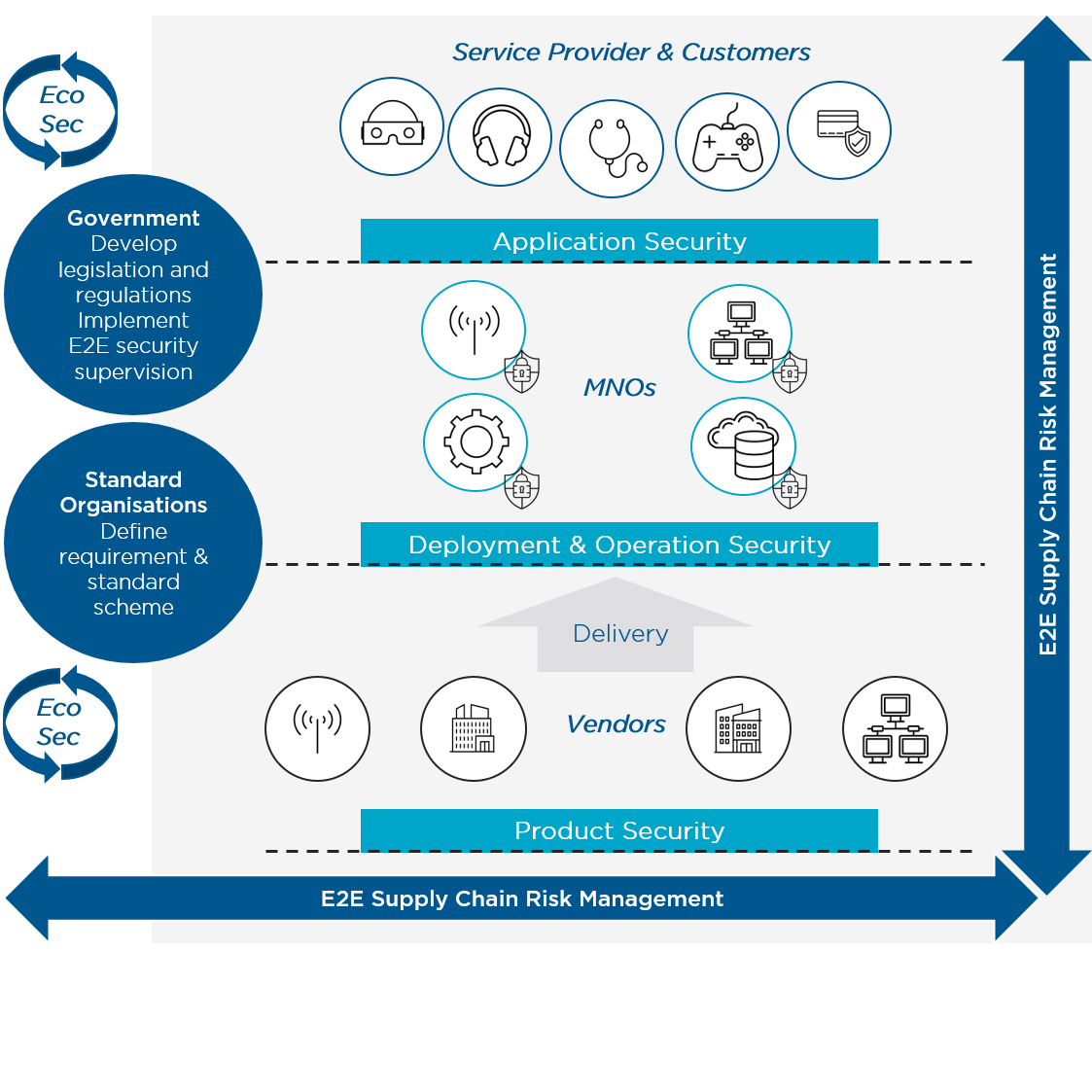
Cybersecurity - a shared responsibility
Mobile cybersecurity is a shared responsibility that involves key stakeholders including MNOs, interconnection providers, vendors, application developers, service providers and governments, each with a clearly defined set of responsibilities which (when fully met) can enable the deployment and operation of mobile systems in a secure manner. The GSMA believes mobile security risks can be addressed through the deployment of coordinated and verifiable security measures based on common standards. The standards provide a solid security foundation and they need to be continuously reviewed and updated to reflect the latest security research and newly identified attack vectors. In addition, MNOs need to constantly evaluate their individual risk and adjust their protections in accordance with the latest mitigation measures and their specific needs.

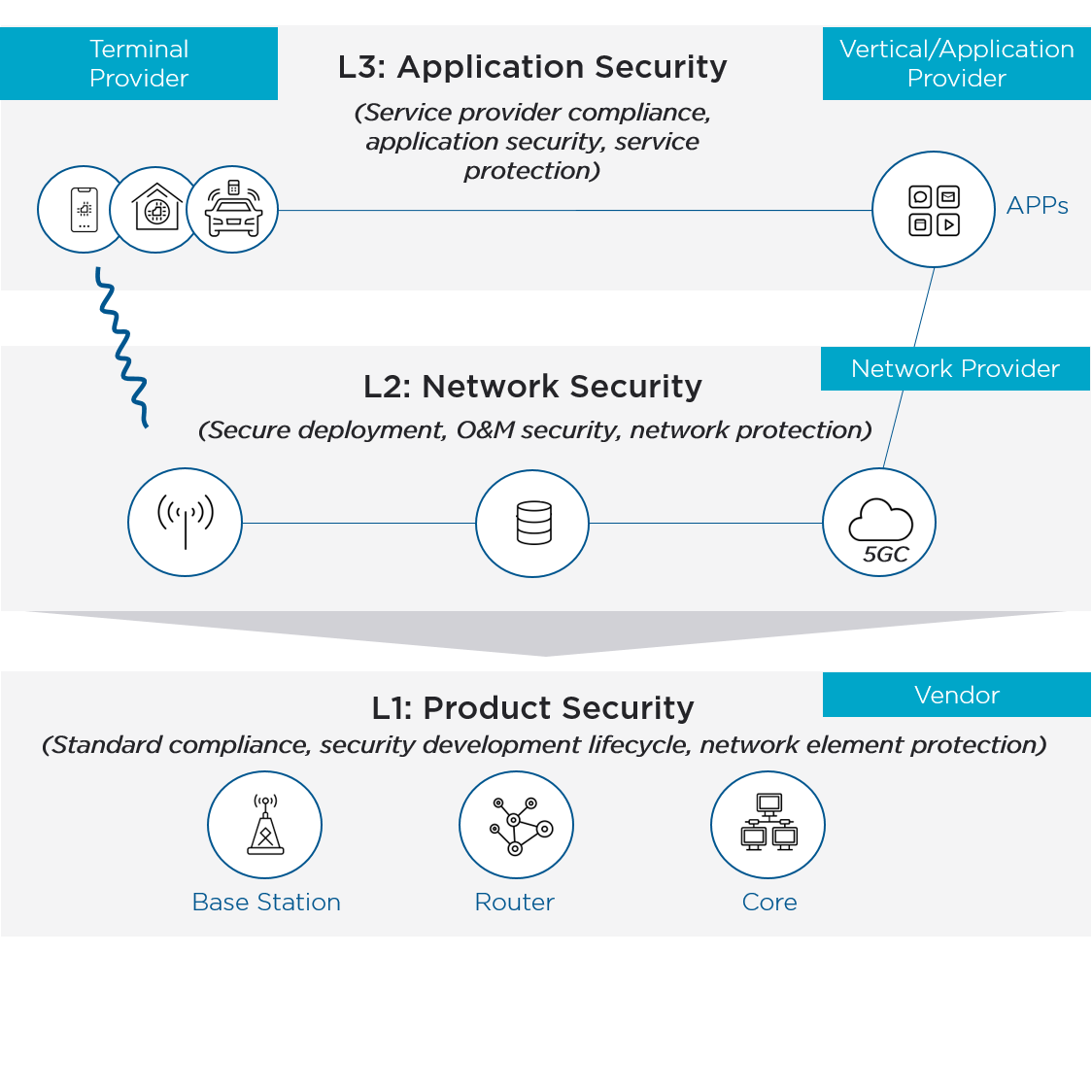
Mobile Cybersecurity – a layered security model
The mobile security model consists of three main layers: application security, network security, and product security.
Application security layer
The scope of the application security layer includes mobile device users (UEs) as well as vertical industries that provide and use a range of applications. Application security requires multi-party collaboration between MNOs, UE vendors, application developers and service providers in order to ensure the security of mobile networks and the users and services they support. Application security extends beyond the MNO networks and, therefore, beyond the responsibility the MNOs. Vertical industries must take responsibility for the security of their solutions. They must introduce mechanisms to protect confidentiality, integrity and availability on top of the built-in security controls offered by MNOs, to further improve the overall security offering. Verticals should ensure that the application layer protects key assets from damage caused by cyber-attacks, that security threats can be identified in a timely manner, and that essential services can be quickly restored. The interaction between verticals and MNOs providing connectivity requires significant collaboration and coordination to ensure optimal filtering, authorisation and authentication, which is managed by the service level agreements between the parties designed to protect against data breaches. In a similar way, security measures between interconnecting MNOs must be designed and enabled to prevent fraud, unauthorised data access and impersonation. These activities require the cooperation of all partners in the interconnection ecosystem.
Network security layer
The network security layer is commonly managed, controlled and operated by the MNO, but some elements might also be outsourced to specialised service providers. During the network design phase, MNOs perform a comprehensive and continuous risk assessment which takes into account network components, network functions provided by vendors and the network architecture to ensure the effective management of security threats.
The signaling, management and data layers all should have automated real-time security detection and control mechanisms. For example, as described in GSMA’s GTP-U Security recommendations (FS.37), both inbound and outbound malicious activities on the data layer can be detected and controlled. Such threats include malware, exploits of network services, command-and-control, application layer attacks, amongst other attacks.
Product security layer
Product security is the responsibility of vendors, such as device providers or network equipment suppliers. Network element security assurance is a key tool, providing a basis to evaluate whether network devices and components have been designed and implemented in accordance with defined security requirements. Security assurance programmes should adhere to globally recognised and unified standards to ensure their operation is cost effective and sustainable for the ecosystem. For example, the Network Equipment Security Assurance Scheme (NESAS), jointly defined by 3GPP and GSMA, provides an industry-wide security assurance framework to facilitate improvements in security levels across the mobile industry. NESAS defines security requirements and an assessment framework for secure product development and product lifecycle processes, as well as using 3GPP defined security test cases for the security evaluation of network equipment. More information about NESAS is available here.

Knowledge Base Documents
Figure: The mobile cybersecurity knowledge base document suite
FS.31 Baseline Security Controls >
Outlines a recommended set of security controls, which map to threats described in FS30, that network operators should consider deploying along with references to relevant standards and other best practice resources. The solution description for each control identifies specific advice that allows the operator to fulfil the control objectives.
FS.30 Security Manual > (Accessible by GSMA Members Only)
Describes range of known threats to which cellular networks and the services they provide could be exposed. The document uses a common taxonomy to describe each threat, its impact, mitigation options and references to aid further understanding.
FS.33 Network Function Virtualisation (NFV) Threats Analysis > (Accessible by GSMA Members Only)
Outlines a comprehensive overview of the threats related to NFV and the underlying hosting infrastructure and platforms. The emphasis of this document is on the security, directly and indirectly, to NFV environments and functions.
FS.37 GTP-U Security > (Accessible by GSMA Members Only)
Provides recommendations for MNOs to detect and prevent attacks using GTP-U plane data on the network, services, and applications and also contains guidelines on how to logically deploy security capabilities (specific interfaces) and the modes of deployment.
FS.57 Mobile Threat Intelligence Framework (MoTIF) Principles >
Specifies a framework for describing, in a structured way, how adversaries attack and use mobile networks, based on the tactics, techniques and procedures (TTPs) that they use. The document defines the techniques and sub-techniques used in the framework and describes how MoTIF can be represented in structured cyber threat language STIX.
FS.34 Key Management for 4G and 5G Inter-PLMN Security >
Outlines the key management process, i.e. the exchange of certificates and key materials that are used between the interconnect parties to secure the signaling communication.
FS.35 Security Algorithm Deployment Guidance > (Accessible by GSMA Members Only)
Outlines the GSM, UMTS, LTE and 5G authentication, privacy and integrity protection algorithms that are used in cellular devices and networks. It provides guidance and recommendations on the best deployment options.
FS.36 5G Interconnect Security > (Accessible by GSMA Members Only)
Outlines potential 5G interconnect based attacks against mobile networks and their customers, and countermeasures for those attacks. It aids understanding of potential risks, threats and countermeasures related to 5G interconnection security to GSMA members.
FS.39 5G Fraud Risks Guide > (Accessible by GSMA Members Only)
Describes potential fraud attacks against 5G networks and the services they support and it recommends countermeasures that can be taken to mitigate the risks posed to network operators and their customers.
FS.40 5G Security Guide >
Contains an overview of the security aspects and capabilities of 5G networks. The document serves as an educational resource that describes the security enhancements and capabilities inherent in 5G technology.